A scripting or script language is a for a special that automates the of tasks; the tasks could alternatively be executed one-by-one by a human operator. Scripting languages are often (rather than ).Primitives are usually the elementary tasks or calls , and the language allows them to be combined into more programs.
Environments that can be automated through scripting include, within a, usage of the of (OS), as well as numerous games. A scripting language can be viewed as a for a particular environment; in the case of scripting an application, it is also known as an extension language. Scripting languages are also sometimes referred to as, as they operate at a high level of abstraction, or as control languages, particularly for job control languages on mainframes.The term 'scripting language' is also used loosely to refer to, such as, and with the term 'script' often used for small programs (up to a few thousand lines of code) in such languages, or in domain-specific languages such as the text-processing languages. Some of these languages were originally developed for use within a particular environment, and later developed into portable domain-specific or general-purpose languages.Conversely, many general-purpose languages have dialects that are used as scripting languages. This article discusses scripting languages in the narrow sense of languages for a specific environment.The spectrum of scripting languages ranges from very small and highly to used for scripting.
Standard examples of scripting languages for specific environments include:, for the or; , for web browsers; and, for applications. Is a language designed and widely used as an extension language. Is a general-purpose language that is also commonly used as an extension language, while ECMAScript is still primarily a scripting language for web browsers, but is also used as a general-purpose language.
The dialect of (for the editor) and the Visual Basic for Applications dialect of are examples of scripting language dialects of general-purpose languages. Some game systems, notably the and the franchise of Railroad simulators have been extensively extended in functionality by scripting extensions ( and ). In other games like, the variety of actual games played by players are scripts written by other users. Contents.Characteristics Typical scripting languages are intended to be very fast to learn and write in, either as short source code files or interactively in a (REPL, language shell). This generally implies relatively simple and; typically a 'script' (code written in the scripting language) is executed from start to finish, as a 'script', with no explicit.For example, it is uncommon to characterise as a scripting language because of its lengthy syntax and rules about which classes exist in which files, and it is not directly possible to execute Java interactively, because source files can only contain definitions that must be invoked externally by a.
This section does not any. Unsourced material may be challenged. ( March 2007) Scripting is often contrasted with, as in or '.
In this view, scripting is particularly, connecting, and a language specialized for this purpose is a glue language. Pipelines and shell scripting are archetypal examples of glue languages, and was initially developed to fill this same role. Can be considered a use of glue languages, interfacing between a. and. (5 and 6).
Sharepoint Online Site Scripts
(, and others).languages exposed to operating system or application components can serve as glue languages. These include, Hummingbird Basic, QuickScript,. Other tools like can also be considered glue languages, as can any language implemented by a engine (VBScript, JScript and VBA by default in Windows and third-party engines including implementations of Rexx, Perl, Tcl, Python, XSLT, Ruby, Modern Pascal, Delphi, and C). A majority of applications can access and use operating system components via the or its own functions.Other devices like programmable calculators may also have glue languages; the operating systems of PDAs such as Windows CE may have available native or third-party macro tools that glue applications together, in addition to implementations of common glue languages—including Windows NT, MS-DOS and some Unix shells, Rexx, Modern Pascal, PHP, and Perl. Depending upon the OS version, WSH and the default script engines (VBScript and JScript) are available.Programmable calculators can be programmed in glue languages in three ways. For example, the, by factory default can be programmed with a command script language.
Inclusion of the scripting and glue language in the series of calculators could be seen as a successor to this. The primary on-board high-level programming languages of most graphing calculators (most often Basic variants, sometimes Lisp derivatives, and more uncommonly, C derivatives) in many cases can glue together calculator functions—such as graphs, lists, matrices, etc. Third-party implementations of more comprehensive Basic version that may be closer to variants listed as glue languages in this article are available—and attempts to implement Perl, Rexx, or various operating system shells on the TI and HP graphing calculators are also mentioned. PC-based C for some of the TI and HP machines used in conjunction with tools that convert between C and Perl, Rexx, AWK, as well as shell scripts to Perl, Modern Pascal, VBScript to and from Perl make it possible to write a program in a glue language for eventual implementation (as a compiled program) on the calculator.Job control languages and shells. Main article:A major class of scripting languages has grown out of the automation of, which relates to starting and controlling the behavior of system programs. (In this sense, one might think of shells as being descendants of IBM's JCL, or, which was used for exactly this purpose.) Many of these languages' interpreters double as such as the or the MS-DOS.
Others, such as offer the use of English-like commands to build scripts.GUI scripting With the advent of graphical user interfaces, a specialized kind of scripting language emerged for controlling a computer. These languages interact with the same graphic windows, menus, buttons, and so on that a human user would. They do this by simulating the actions of a user.
These languages are typically used to automate user actions. Such languages are also called ' when control is through simulated key presses or mouse clicks, as well as tapping or pressing on a touch-activated screen.These languages could in principle be used to control any GUI application; but, in practice their use is limited because their use needs support from the application and from the. There are a few exceptions to this limitation. Some GUI scripting languages are based on recognizing graphical objects from their display screen. These GUI scripting languages do not depend on support from the operating system or application.Application-specific languages Application specific languages can be split in many different categories, i.e. Standalone based app languages (executable) or internal application specific languages (postscript, xml, gscript as some of the widely distributed scripts, respectively implemented by Adobe, MS and Google) among others include an idiomatic scripting language tailored to the needs of the application user.
Likewise, many systems use a custom scripting language to express the programmed actions of and the game environment. Languages of this sort are designed for a single application; and, while they may superficially resemble a specific general-purpose language (e.g., modeled after C), they have custom features that distinguish them., while a fully formed and capable dialect of, contains many special features that make it most useful for extending the editing functions of Emacs. An application-specific scripting language can be viewed as a specialized to a single application.Extension/embeddable languages A number of languages have been designed for the purpose of replacing application-specific scripting languages by being embeddable in application programs.
The application programmer (working in C or another systems language) includes 'hooks' where the scripting language can control the application. These languages may be technically equivalent to an application-specific extension language but when an application embeds a 'common' language, the user gets the advantage of being able to transfer skills from application to application. A more generic alternative is simply to provide a library (often a C library) that a general-purpose language can use to control the application, without modifying the language for the specific domain.JavaScript began as and primarily still is a language for scripting inside; however, the standardisation of the language as has made it popular as a general-purpose embeddable language. In particular, the implementation is embedded in several environments such as the. Other applications embedding ECMAScript implementations include the products and (for scripting files).was created as an extension language but has come to be used more frequently as a general-purpose language in roles similar to,.
On the other hand, was originally created as a job control language, but is widely used as an extension language as well as a general-purpose language. Perl is a general-purpose language, but had the Oraperl (1990) dialect, consisting of a 4 binary with compiled in. This has however since been replaced by a library (Perl Module),.Other complex and task-oriented applications may incorporate and expose an embedded programming language to allow their users more control and give them more functionality than can be available through a user interface, no matter how sophisticated. For example, 3D authoring tools embed the scripting language, or which uses to fill this role.Some other types of applications that need faster feature addition or tweak-and-run cycles (e.g. ) also use an embedded language. During the development, this allows them to prototype features faster and tweak more freely, without the need for the user to have intimate knowledge of the inner workings of the application or to rebuild it after each tweak (which can take a significant amount of time). The scripting languages used for this purpose range from the more common and more famous and to lesser-known ones such as and.is another C compatible scripting option for the industry to embed into C/C application programs.See also.
/.References.
Cross-site Scripting (XSS) is a client-side code. The attacker aims to execute malicious scripts in a web browser of the victim by including malicious code in a legitimate web page or web application. The actual attack occurs when the victim visits the web page or web application that executes the malicious code. The web page or web application becomes a vehicle to deliver the malicious script to the user’s browser. Vulnerable vehicles that are commonly used for Cross-site Scripting attacks are forums, message boards, and web pages that allow comments.A web page or web application is vulnerable to XSS if it uses unsanitized user input in the output that it generates.
This user input must then be parsed by the victim’s browser. XSS attacks are possible in VBScript, ActiveX, Flash, and even CSS. However, they are most common in JavaScript, primarily because JavaScript is fundamental to most browsing experiences.“Isn’t Cross-site Scripting the User’s Problem?”If an attacker can abuse an XSS vulnerability on a web page to execute arbitrary JavaScript in a user’s browser, the security of that vulnerable website or vulnerable web application and its users has been compromised. XSS is not the user’s problem like any other security vulnerability. If it is affecting your users, it affects you.Cross-site Scripting may also be used to instead of targeting the user.
The attacker can use injected scripts to change the content of the website or even redirect the browser to another web page, for example, one that contains malicious code. What Can the Attacker Do with JavaScript?XSS vulnerabilities are perceived as less dangerous than for example vulnerabilities. Consequences of the ability to execute JavaScript on a web page may not seem dire at first. Most web browsers run JavaScript in a very tightly controlled environment. JavaScript has limited access to the user’s operating system and the user’s files. However, JavaScript can still be dangerous if misused as part of malicious content:.
Malicious JavaScript has access to all the objects that the rest of the web page has access to. This includes access to the user’s cookies. Cookies are often used to store session tokens.
If an attacker can obtain a user’s session cookie, they can impersonate that user, perform actions on behalf of the user, and gain access to the user’s sensitive data. JavaScript can read the browser DOM and make arbitrary modifications to it. Luckily, this is only possible within the page where JavaScript is running. JavaScript can use the XMLHttpRequest object to send HTTP requests with arbitrary content to arbitrary destinations.
JavaScript in modern browsers can use HTML5 APIs. For example, it can gain access to the user’s geolocation, webcam, microphone, and even specific files from the user’s file system. Most of these APIs require user opt-in, but the attacker can use social engineering to go around that limitation.The above, in combination with social engineering, allow criminals to pull off advanced attacks including cookie theft, planting trojans, keylogging, phishing, and identity theft. XSS vulnerabilities provide the perfect ground to escalate attacks to more serious ones. Cross-site Scripting can also be used in conjunction with other types of attacks, for example,.There are several types of Cross-site Scripting attacks:,. You can read more about them in an article titled. How Cross-site Scripting WorksThere are two stages to a typical XSS attack:.
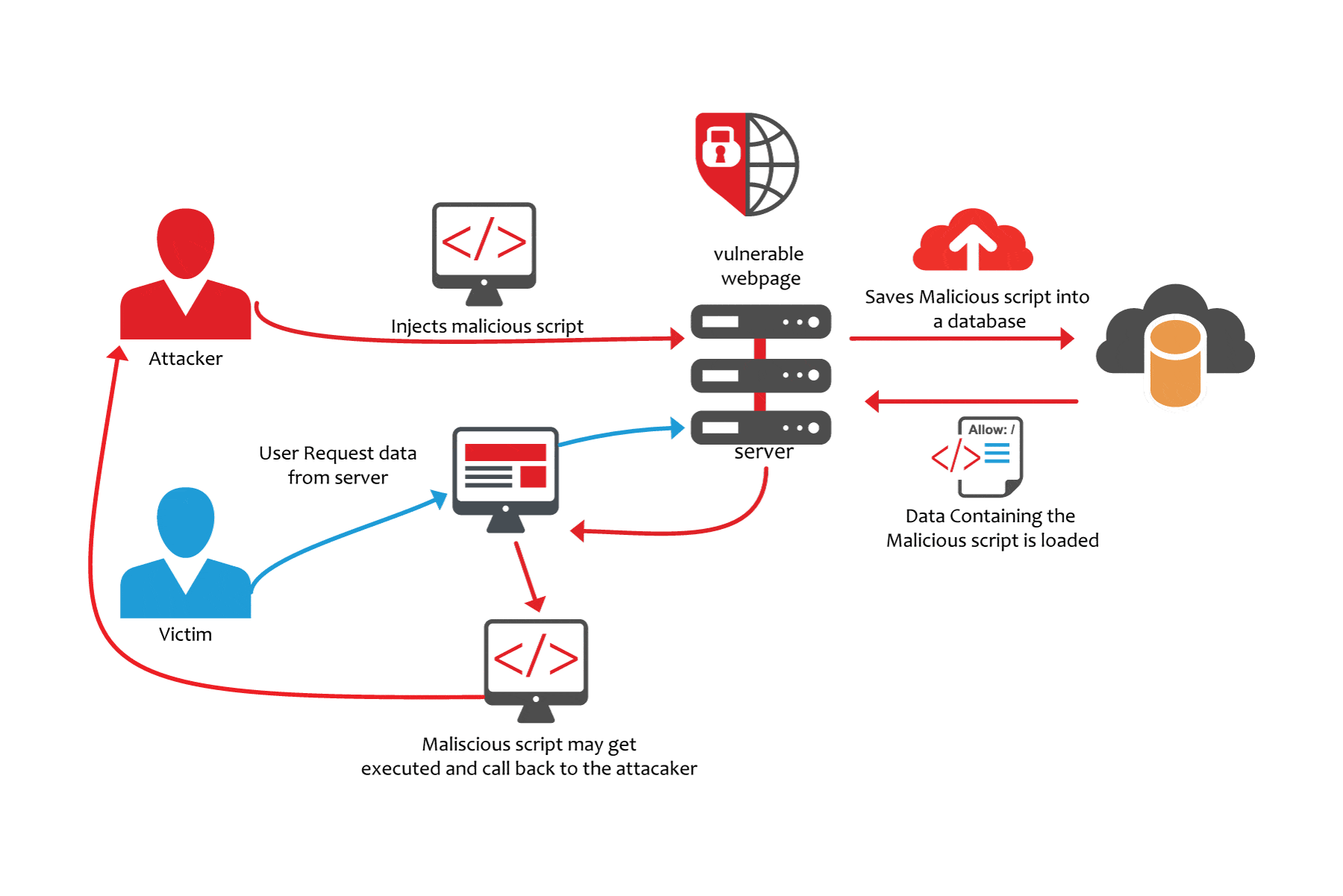
To run malicious JavaScript code in a victim’s browser, an attacker must first find a way to inject malicious code (payload) into a web page that the victim visits. After that, the victim must visit the web page with the malicious code. If the attack is directed at particular victims, the attacker can use social engineering and/or phishing to send a malicious URL to the victim.For step one to be possible, the vulnerable website needs to directly include user input in its pages. An attacker can then insert a malicious string that will be used within the web page and treated as source code by the victim’s browser. There are also variants of XSS attacks where the attacker lures the user to visit a URL using social engineering and the payload is part of the link that the user clicks.The following is a snippet of server-side pseudocode that is used to display the most recent comment on a web page: print 'print 'Most recent comment'print database.latestCommentprint 'The above script simply takes the latest comment from a database and includes it in an HTML page. It assumes that the comment printed out consists of only text and contains no HTML tags or other code. It is vulnerable to XSS, because an attacker could submit a comment that contains a malicious payload, for example: doSomethingEvil;The web server provides the following HTML code to users that visit this web page: Most recent commentdoSomethingEvil;When the page loads in the victim’s browser, the attacker’s malicious script executes.
Most often, the victim does not realize it and is unable to prevent such an attack. Stealing Cookies Using XSSCriminals often use XSS to steal cookies. This allows them to impersonate the victim. The attacker can send the cookie to their own server in many ways.
One of them is to execute the following client-side script in the victim’s browser: window.location='+ document.cookieThe figure below illustrates a step-by-step walkthrough of a simple XSS attack. The attacker injects a payload into the website’s database by submitting a vulnerable form with malicious JavaScript content. The victim requests the web page from the web server. The web server serves the victim’s browser the page with attacker’s payload as part of the HTML body. The victim’s browser executes the malicious script contained in the HTML body. In this case, it sends the victim’s cookie to the attacker’s server. The attacker now simply needs to extract the victim’s cookie when the HTTP request arrives at the server.
The attacker can now use the victim’s stolen cookie for impersonation.To learn more about how XSS attacks are conducted, you can refer to an article titled. Cross-site Scripting Attack VectorsThe following is a list of common XSS attack vectors that an attacker could use to compromise the security of a website or web application through an XSS attack. A more extensive list of XSS payload examples is maintained by the OWASP organization:. TagThe